Briefly Explain Different Types of Security Services
These services are intended to counter security attacks and they make use of one or more security mechanisms to provide the service. Contact Us Today for a Complimentary in-Home Assessment.

Computer System Components Computer System What Is Computer Characteristics Of Computer
Keep Yourself and Your Property Secure.
. Its like your own personal protection wall. Encipherment - encrypting and decrypting communicationdigital signatures - an electronic signature to assure the genuineness of a digital documentaccess controls - to only allows people with. Network End-Point and Internet security the cybersecurity subcategory.
Equity securities which includes stocks Debt securities which includes bonds and banknotes Derivatives which includes options and futures Types of Securities 1. It is achieved by applying mathematical calculations or algorithms which reconstruct information into not readable form. These are security guards that will patrol your location on foot or in a vehicle.
Types of Security attacks Active and Passive attacks. Available to authorized entities for 247. This is hiding or covering of data which provides confidentiality.
Network Security List and briefly define categories of security services Answer the following question. Types of Computer Security. There are three primary areas or classifications of security controls.
What are the essentials ingredients of a symmetric cipher. Controls who can have access to resource under what condition. List and briefly define categories of security services.
In this post we will focus on the different types of computer security such as application security network security internet security data security information security and end user security. Ad Easily Review Top Home Security Companies Start Protecting Your Home Today. The confidentiality of selected fields within the user Data.
It is also used to complement other mechanisms to provide other services. If you have a large premises or a multiple location that you want to protect you can hire a mobile patrol security. Malicious hackers can go about this in a variety of ways including the ones listed below.
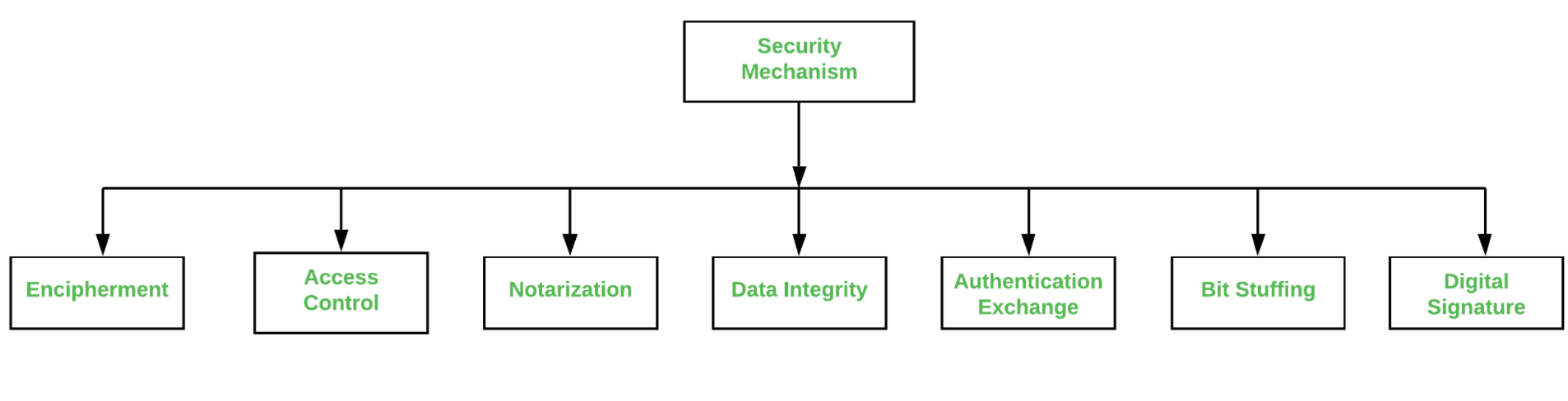
List and briefly define categories of security mechanisms 10 marks Q3. Authentication can be done by sending digital signature. The protection of all user data in a single data block Selective-Field Confidentiality.
Security poses a major challenge to the widespread adoption of cloud computing yet an association of cloud users and vendors sees the cloud as a provider of information security services. Cryptography and Steganography are used for enciphering 2. Equity securities Equity almost always refers to stocks and a share of ownership in a company which is possessed by the shareholder.
There are different methods to check the genuineness of the sender. GPS Security uses advanced technology that allows the client to conduct real time tracking of the patrol unit. An Active attack attempts to alter system resources or effect their operations.
Types of Security Mechanism are. 1 Answer 2 17k views written 58 years ago by teamques10 16k The various security mechanisms to provide security are as follows- 1. Mobile Patrol Security Service.
Active attack involve some modification of the data stream or creation of false statement. Security and Risk Services. This security will work to protect the usability and integrity of your network and data.
Assures recipient that the message is from the source that it claims to be from. Review The Best Home Security Systems in 1 Easy site Protect Your Home Today. Authentication These services provide for the authentication of a communicating peer entity and the source of data as described below.
Malicious software malware infects devices without users realizing its there. However for the most part there are three broad types of IT security. Ad Customized Security Services.
A trusted third party verifies the authenticity. Were Dedicated to Your Safety and Well-Being. Furthermore as networks continue to expand with the cloud and other new technologies more types of IT security will emerge.
Masquerade attack takes place when one entity pretends to be different entity. A processing or communication service that enhances the security of the data processing systems and the information transfers of an organization. Connection ConfidentialityThe protection of all user data on a connection.
Following are the five categories of these services. There are three main types of security officers working for private and public businesses and individuals. Peer entity authentication This service when provided by the N-layer provides corroboration to the N 1-entity that the peer entity is the claimed N 1-entity.
Network security works by identifying and targeting a variety of threats then stops them from entering your network. One of the most important types of security you should have is network security. It is achieved by two famous techniques named Cryptography and Encipherment.
Each security expert has their own categorizations. The other various types of IT security. Within those three main types there are even more options armed and unarmed plainclothes or uniformed on-site or remote.
These include management security operational security and physical security controls. The two parties share a common secret code word. Government in-house and those working contractually for private security firms.
Managed Security Services. CDW Can Help Protect You from Costly Data Breaches Through a Cohesive Security Strategy. Ad CDW Cybersecurity Solutions Offer Tailor-Made Protection for Your Organization.
Variations include Trojan horses spyware ransomware malvertising and viruses. A party is required to show the secret code word to the other for authentication. This security mechanism deals with hiding and covering of data which helps data to become confidential.
Types of active attacks are as following.

Types Of Storage Devices Advantages With Examples In 2022 Storage Devices Storage Magnetic Tape

Types Of Security Mechanism Geeksforgeeks
